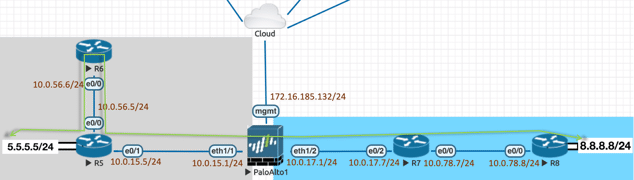
It took me about 2 hours on the following scenario and the root cause was located: lacking a static route on Palo Alto, so I decided to summarize every step here for further reference. Here is the topology on EVE-NG:
- The left part is the office, and the right part is Internet
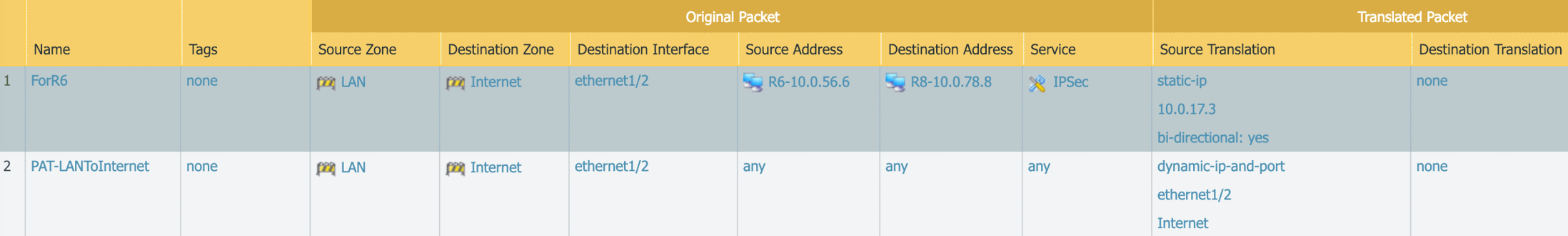
- 10.0.56.5 of R6 was NATed to IP: 10.0.17.3 by Palo Alto which establishes IPSec tunnel with R8: 10.0.78.8
- Traffic from 5.5.5.0/24 to 8.8.8.0/24 will be forward over the #1 IPSec
- All device in ‘LAN’ could access ‘Internet’ via Port Translation
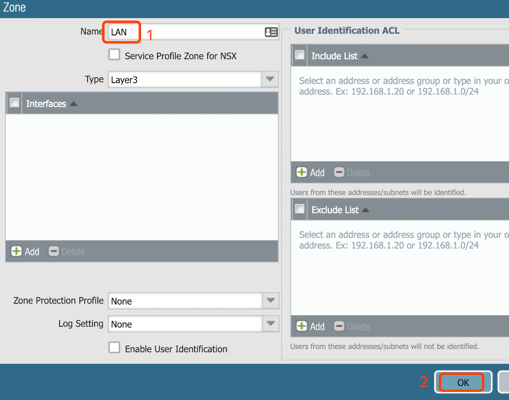
1. Initial Palo Alto
Console access Palo Alto with username/password: admin/admin, and configure MGMT IP 172.16.185.132 (I have bridged the MGMT interface of Palo Alto to my laptop). Here are the commands for the initialization:
configure
edit deviceconfig system
set ip-address 172.16.185.132 netmask 255.255.255.0
commit
Note: Executing ‘commit’ on CLI or Web GUI after the modification.
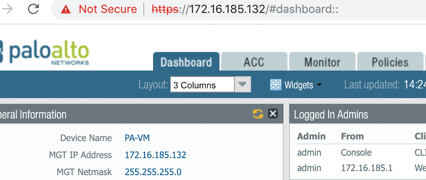
2. Navigate https://172.16.185.132 (MGMT IP of Palo Alto Firewall) in the browser
login with the username/password: admin/admin (default username/password)
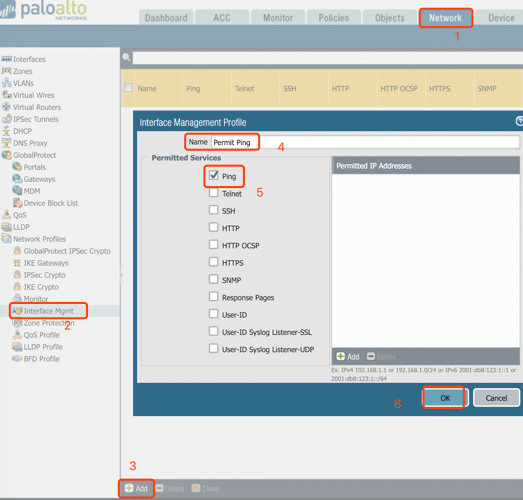
3. Configure Interface Profiles
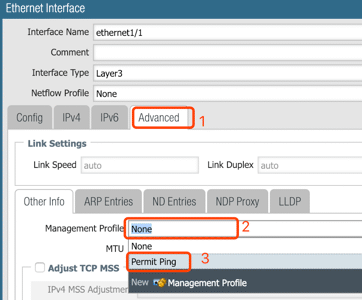
Policy: Permit ping traffic from both LAN and Internet to Palo Alto interfaces for connectives testing
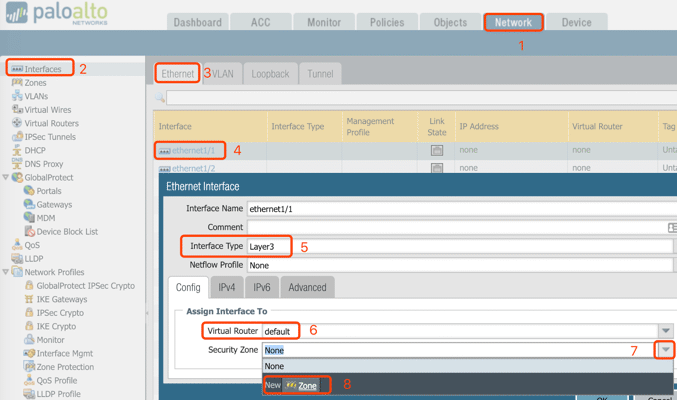
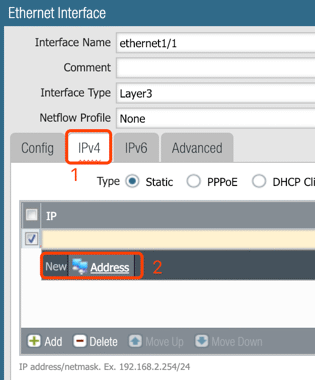
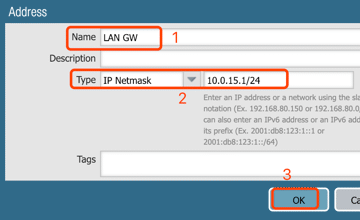
4. Configure interface: ethernet1/1
5. Configure interface: ethernet1/2
Almost the same steps to ethernet1/1 but with different IP and Zone – IP: 10.0.17.1/24, Zone: Internet.
6. Configured IPs, routing protocol on R5, R6, R7, R8 then run connectivity testing.
- R5: Ethernet0/0 – 10.0.56.5/24, Ethernet0/1 – 10.0.15.5/24, Loopback0: 5.5.5.5/24, Default route with gateway: 10.0.15.1
- R6: Ethernet0/0 – 10.0.56.6/24, Default route with gateway: 10.0.56.5
- R7: Ethernet0/0 – 10.0.78.7/24, Ethernet0/2 – 10.0.17.7/24
- R8: Ethernet0/0 – 10.0.78.8/24, Loopback0 – 8.8.8. /24, Static route to 10.0.17.0/24 with next hop: 10.0.78.7
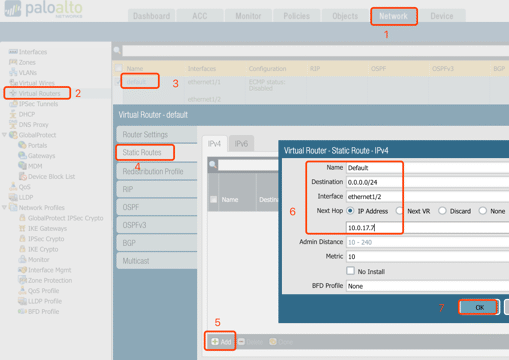
7. Configure routing on Palo Alto
Default route with the next hop: 10.0.17.7
A static route to 10.0.56.0/24 with the next hop 10.0.15.5
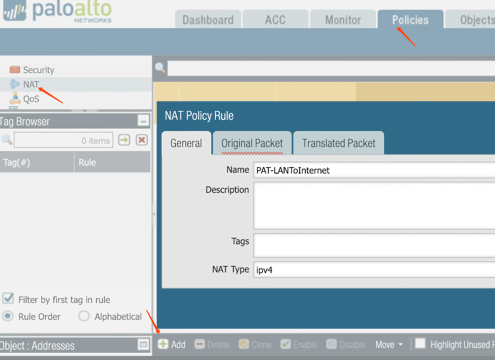
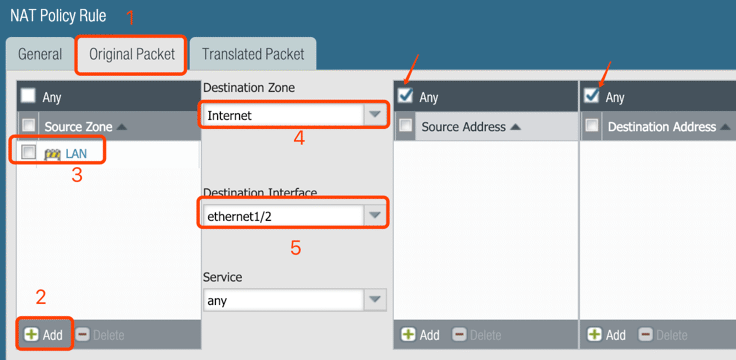
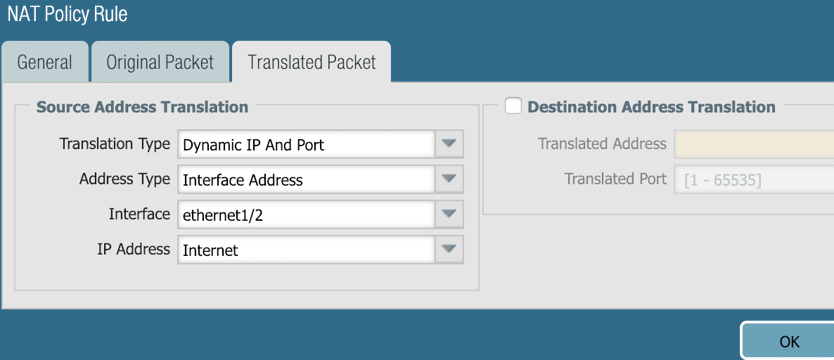
8. Configure PAT for Requirement #4: traffic from LAN to the Internet
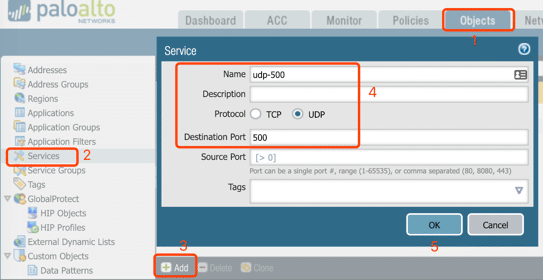
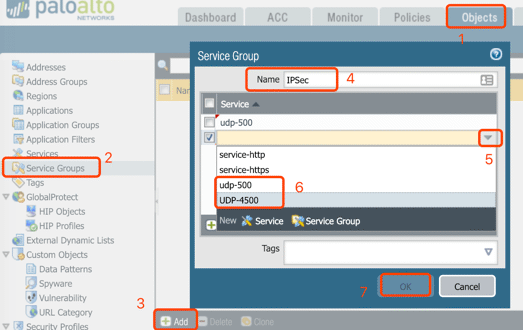
9. Service Group
Creating Service and Security Group before the Security policy for IPSec traffic: UDP 500 and UDP 4500
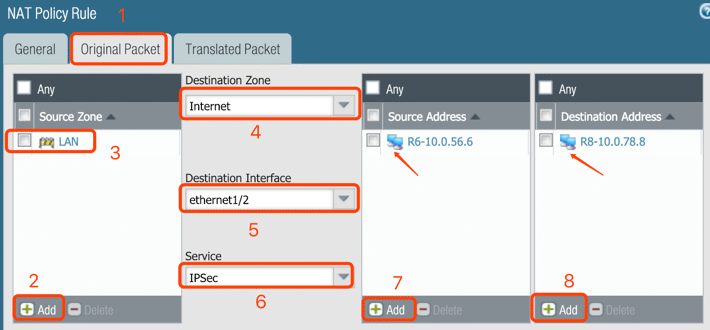
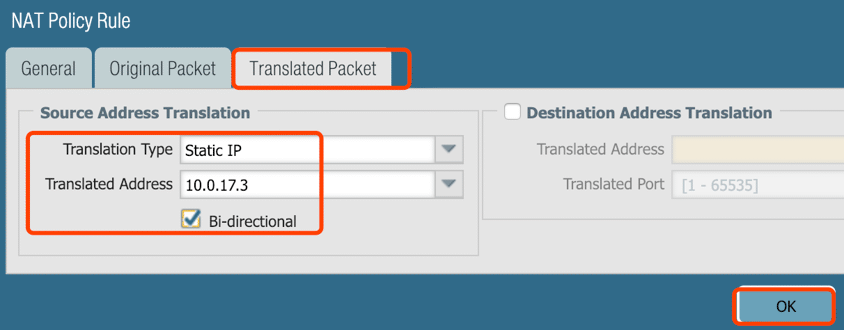
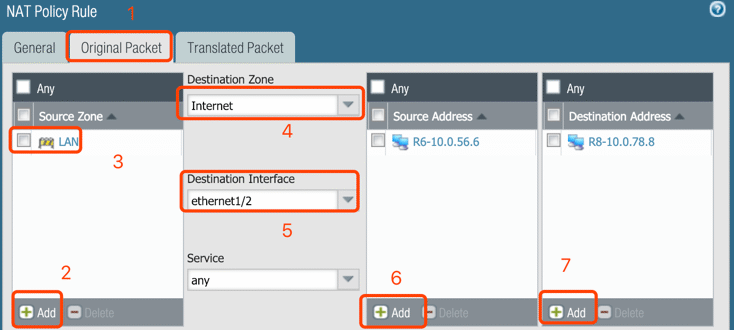
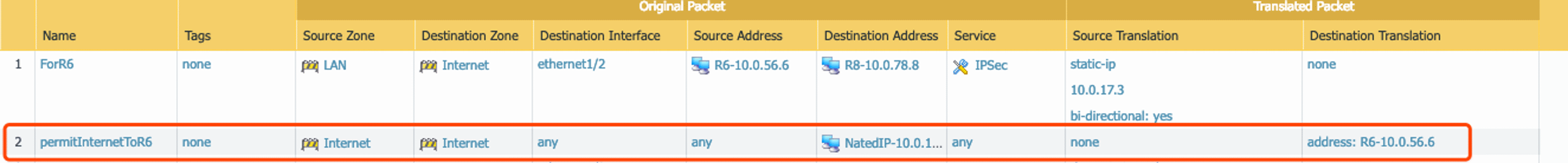
10. Configure NAT for requirement #3 – IPSec
Note: The destination address is the IP of Peer IP, the IP is:10.0.78.8 /32 in my case.
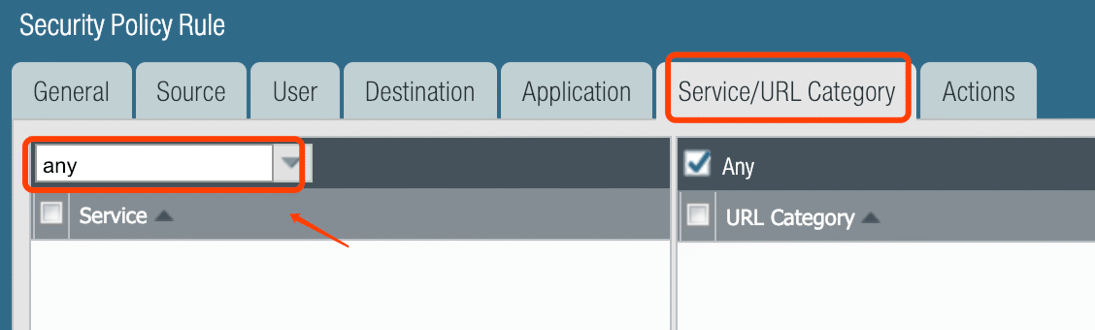
Optional: Set Service to ‘Any’ for all applications
Palo Alto-NAT/PAT-Overall view of Step 9 and Step 10
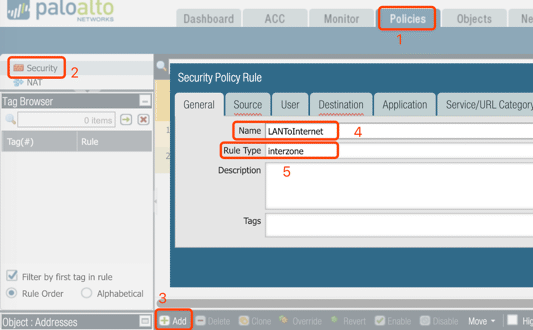
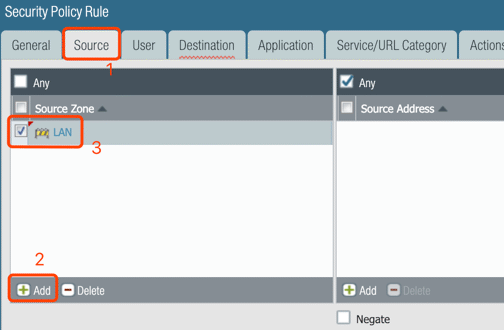
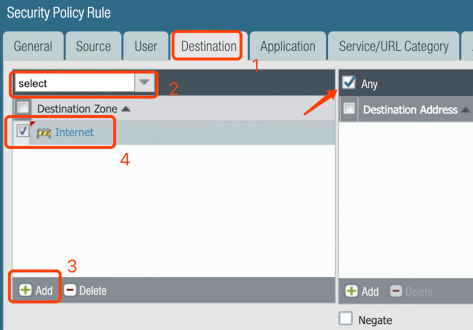
11. Policy for LAN/Internet
Since LAN and Internet are two different zones, security policies are required for the traffic. From LAN to Internet:
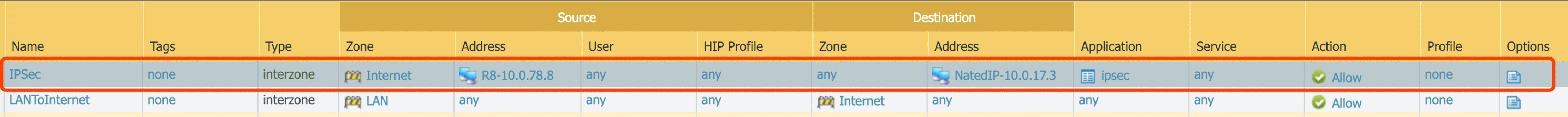
12. Security policy for IPSec
13. Verify connectives on all routers
Note: Security policy for Ping traffic in two different Zones, Ping will fail if only the application: ICMP was permitted, the service: ‘Ping’ is also required.
14. Configure IPSec on R6 and R8.
Check all routers configuration from here.
15. On R5, execute ‘ping 8.8.8.8 source 5.5.5.5’
LAN-R5#ping 8.8.8.8 source 5.5.5.5
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
Packet sent with a source address of 5.5.5.5
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/3/7 ms
LAN-R6#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
10.0.78.8 10.0.56.6 QM_IDLE 1001 ACTIVE
IPv6 Crypto ISAKMP SA
Internet-R8#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
10.0.78.8 10.0.17.3 QM_IDLE 1001 ACTIVE
IPv6 Crypto ISAKMP SA
Others
Permit the ICMP traffic to NATed IP for monitoring purpose [Udate @ 2019-02-14]
For outside interface (Port Translation)
It’s eth1/2 in this case, please refer to 13. Verify connectives on all routers - interface management profile configuration.
For NATed IP
Setup the NAT:
Update both source IP of NAT entry and Security policy for IPSec to permit the traffic in.
Note: For the Security policy:Servicefield should beany,icmpmust be defined inApplicationfield.Reference: Dynamic IP and Port NAT for ICMP traffic
Scan the QR code using WeChat